The main content of this topic is to simulate a TCP syn flood attack against my Aliyun host in order to have some tests. With the help of the kamene framework which also known as scapy3, I’ll craft some IP packets as we always did with Rawsocket of C under unix years ago, at the same time to notes some concerns during this process, including how it works, the network topology, the usage of kamene, the configuration of the firewall, and the packets dump of the server.
How It Works
The idea is very simple. SYN queue flood attack takes advantage of the TCP protocol’s “three-way handshake”, the client send a “SYN”, the server answer a “SYN, ACK”, and the client do nothing but leave the connection half opened. This action will repete again and again to consume the server’s resources as much as possible.
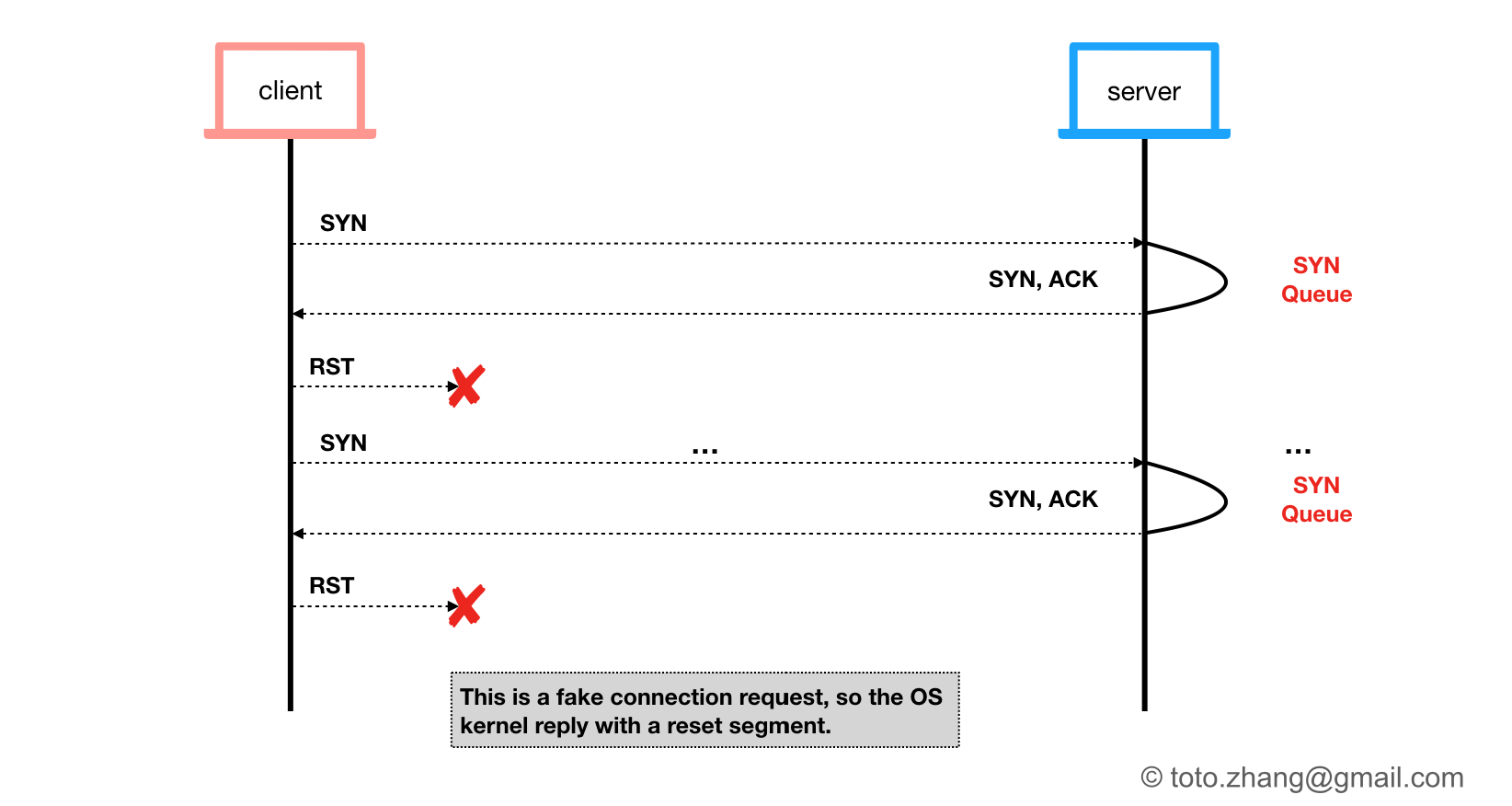
One Packet Test
The code send one packet to the host 47.95.194.185, it’s a tcp SYN packet.
1 | from kamene.all import * |
Run this code, and capture the packets on the client side and server side. The client (macOS) sends a RST after receiving the SYN, ACK from the server to notify the server not to allocate resources for this request. So what I need to do is stop this RST being sent out.
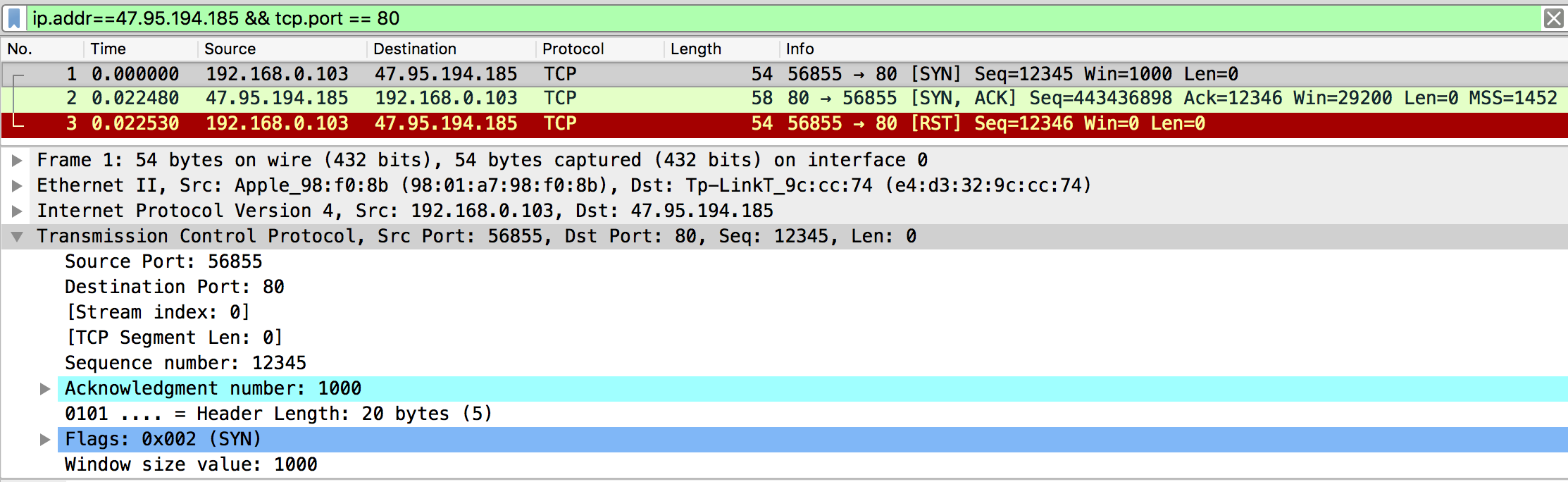
Because the client is behind the NAPT and the server is also behind the NAPT.
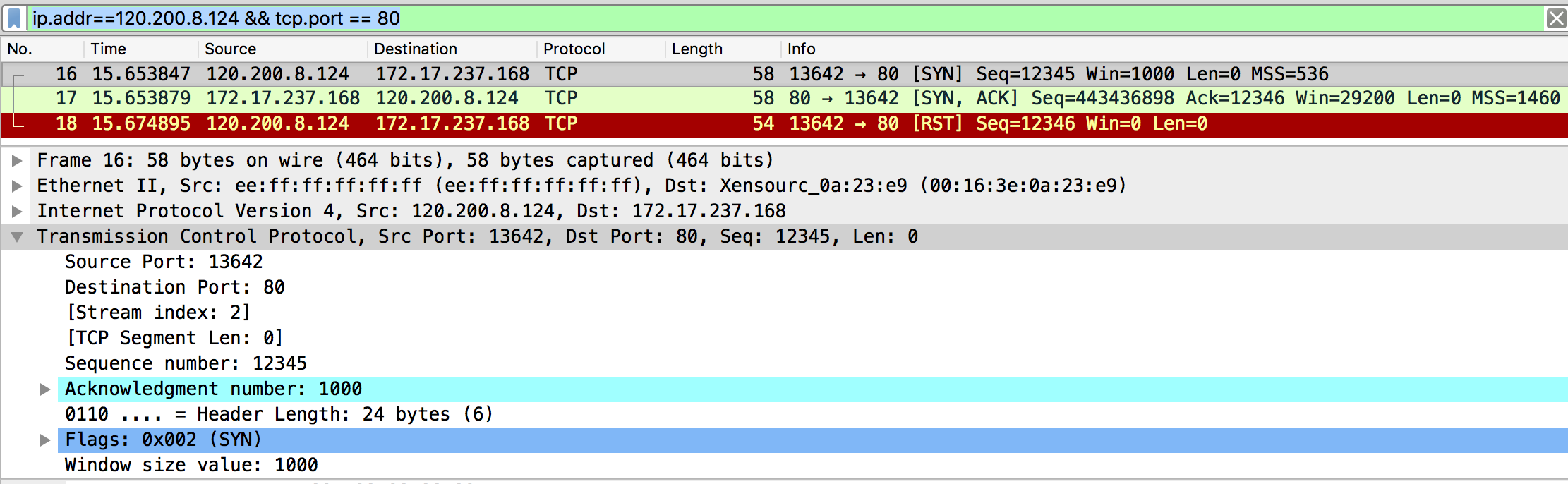
Config Firewall To Stop The RST
On the client macOS, append this line into /etc/pf.conf, and reboot the system.
1 | block drop proto tcp from any to any flags R/R |
After the computer boots up, make sure the firewall is working.
1 | > sudo pfctl -e |
Run the script again, and check out the wireshark captures, RST has been blocked by the firewall.

Finish The Works
Finish the code to loop the packet sending activity,
1 | from kamene.all import * |
Check the server tcp connection status, we can see the number of connections that are in the SYN_RECV status is increasing, if I change the code to send the packet quick enough, the server will deny to service the other customers.
1 | root@iZ2ze0ycbhz8v1bg7bckj8Z:~# netstat -anp | grep 8080 |
What if the 3-way-handshake complete
The firewall is enabled, and I send the final ack of the 3-way-handshake to establish the connection, what will happen?
1 | from kamene.all import * |
Run this code and capture the packets in wireshark.
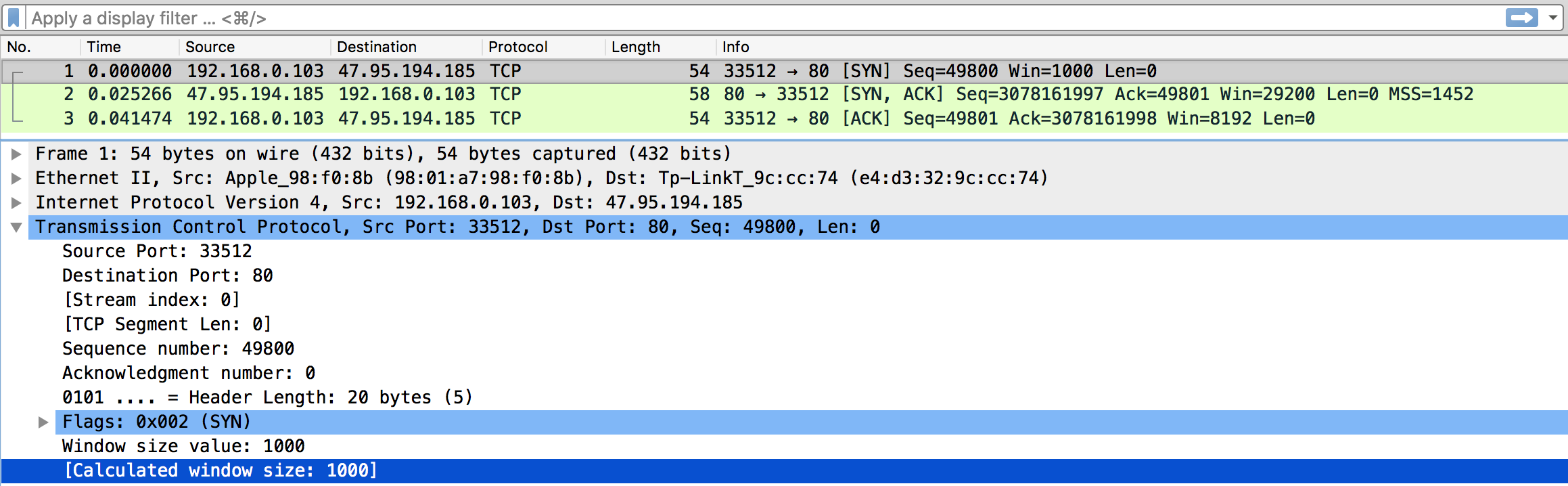
Check out the network status on the server, a connection has been established successfully.
1 | root@iZ2ze0ycbhz8v1bg7bckj8Z:~# netstat -anp | grep 120.200.8.124 |
Check out the network status on the client, there’s no connection infomation to the server.
1 | ➜ ~ netstat -an | grep 47.95.194.185 |