TCP connection can be established by SYN segmentation initiated by both ends to the other party at the same time. At the same time, the established connection must meet one condition. After SYN connection request is issued by both TCP ends, a SYN connection request is still received, and the SYN received is exactly from the end that sent SYN to request connection.So is there a situation like this? A TCP end issues a SYN segment to itself, and the connection requested by the SYN segment is exactly the TCP end itself, which meets the condition of “SYN request is received at the same time as SYN request, and the SYN received happens to be from the end of the requesting connection”. This situation is real and is called TCP self-connection. The existence of self-connectivity often causes inexplicable problems and hard-to-reproduce failures and software bugs.
Connection Sequence
The segments interaction sequence of TCP connection at the same time, 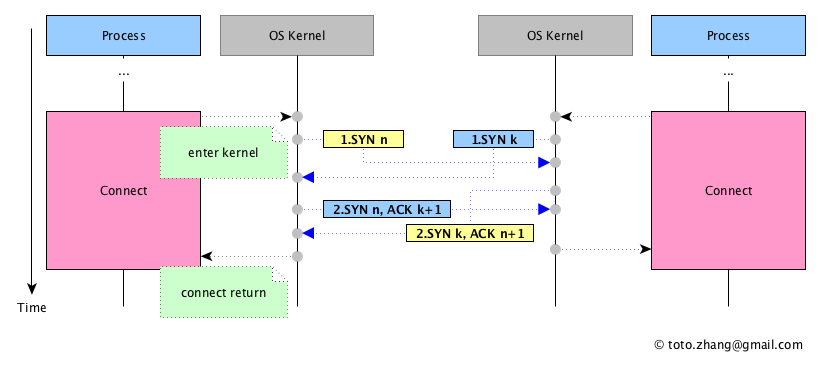
Now we make some modification to the diagram and compare it with the previous one?Instead of [1.syn k], [1.syn n] is sent to itself other than to the other endpoint, here n equals to k. 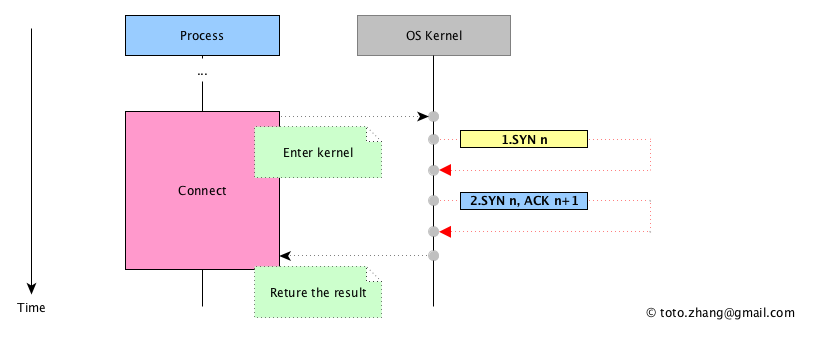
After the connection is established, the connection situation is as follows: 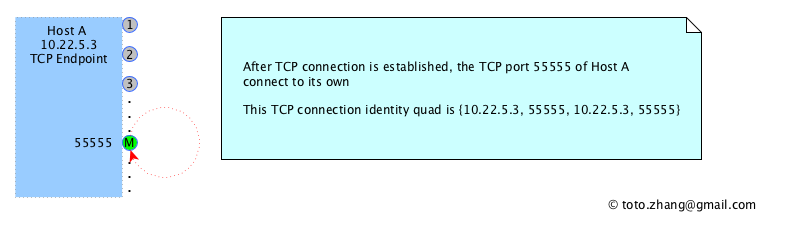
When the connection is disconnected, the interaction sequence is similar to the establishment of the connection. 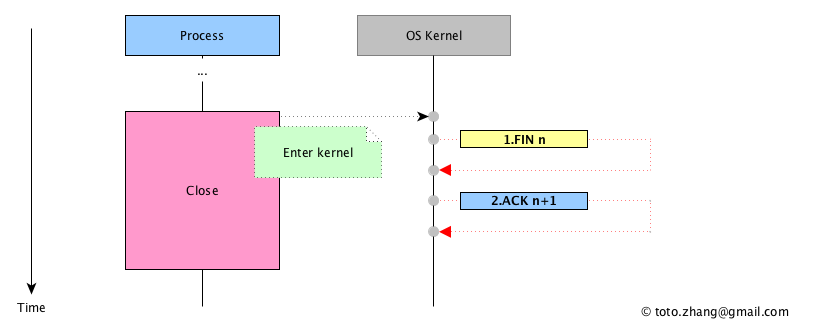
An example of self connection
Now we reproduce the self-connection senario with the following code, only client.c is required here.
Code
1 | //client.c |
Self-connection establishment
On the host 10.22.5.3, execute client with parameters argv1 55555,argv2 10.22.5.3,argv3 55555, 1
2toto@guru:~$ client 55555 10.22.5.3 55555
request,hostname
Single step run the client to function Connect() with Gdb, check the TCP connection status, 1
2toto@guru:~$ netstat -ant | grep 55555
tcp 0 0 10.22.5.3:55555 10.22.5.3:55555 ESTABLISHED
When the instance runs, Wireshark is used to retrieve TCP segment data [1.syn n], [2.syn n, ACK k+1], and the details are as follows, from 10.22.5.3:55555 to 10.22.5.3:55555 to initiate a SYN connection request. ISN for 787485307. 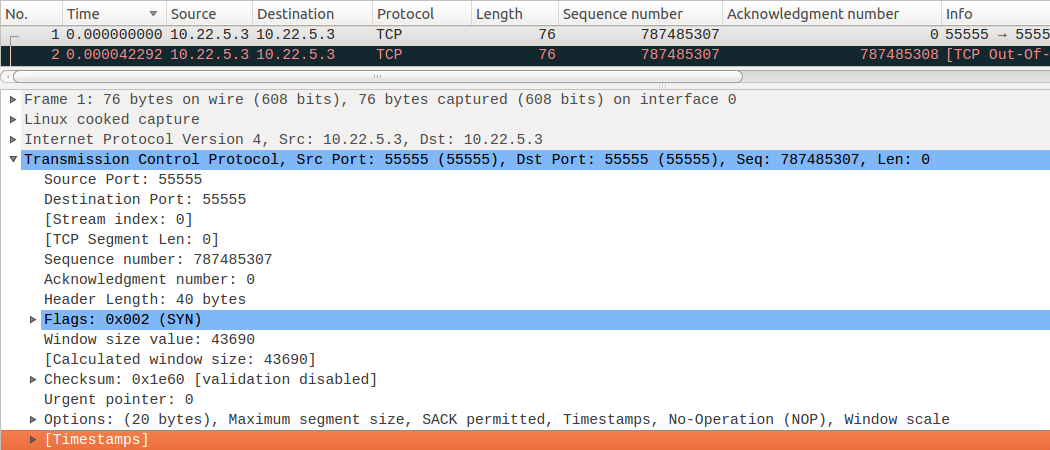 Initiate SYN, ACK from 10.22.5.3:55555 to 10.22.5.3:55555. ACK for 787485308.
Initiate SYN, ACK from 10.22.5.3:55555 to 10.22.5.3:55555. ACK for 787485308. 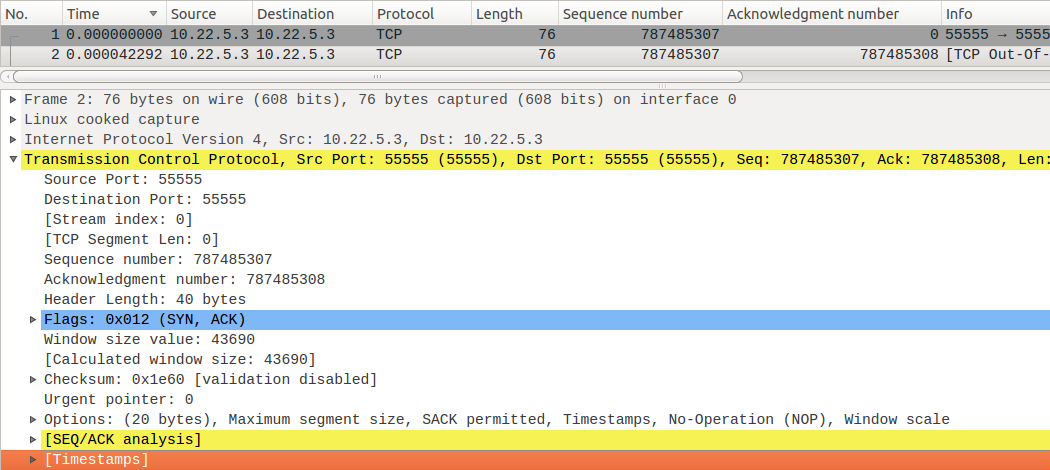
Self-connection disconnect
Running until the end of the process, Wireshark is used to obtain TCP segment data [1.fin n], and the details of [2.ack n+1] are as follows: 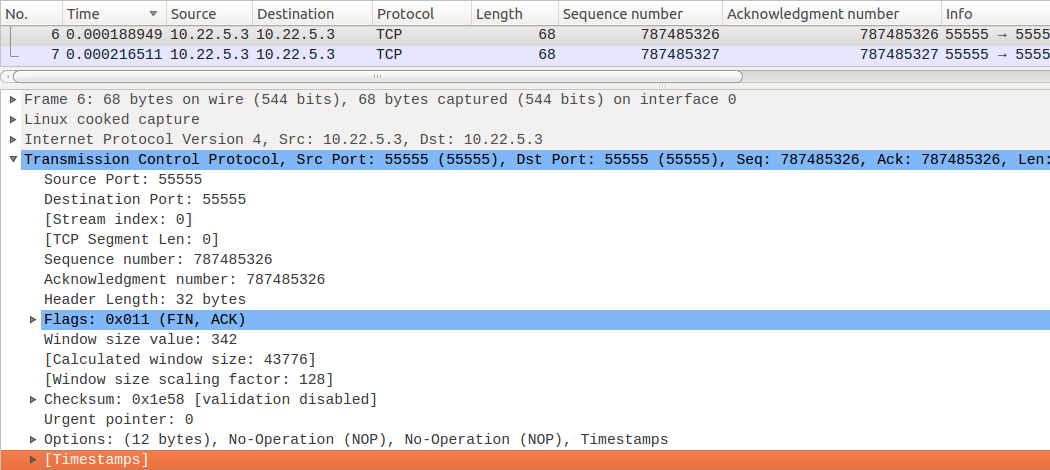
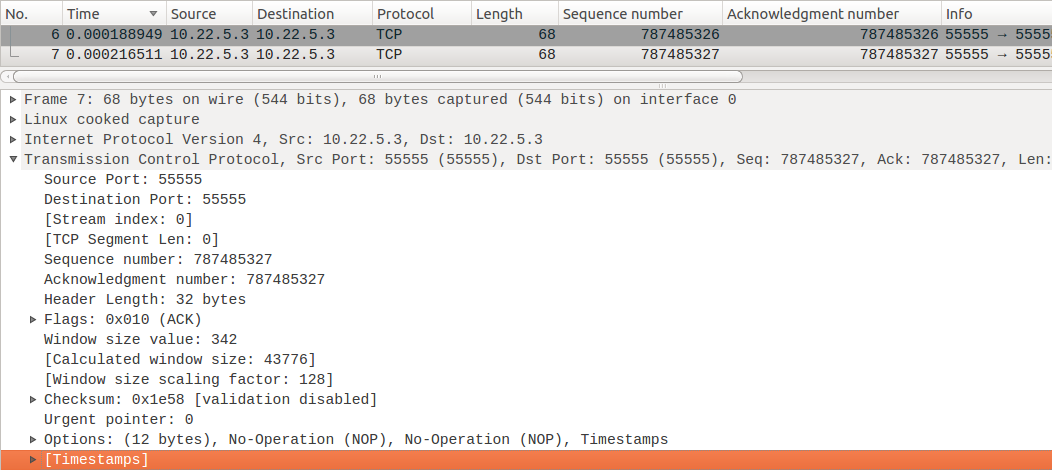
Check the TCP connection status, 1
2toto@guru:~$ netstat -ant | grep 55555
tcp 0 0 10.22.5.3:55555 10.22.5.3:55555 TIME_WAIT
Avoid self-connection problems
TCP self-connection occurs because both the client and the server are located on the same host, and the server port is within the scope of the random port used by the client system, and the client frequently establishes TCP connection. For example, the current host provides the client with a temporary port range of [32768,61000], which may cause TCP self-connection when the port within this range is selected as the service port. Therefore, attention should be paid to the design.
1 | #View temporary port ranges available under Linux |